Imagine how numerous the sector relies on the net. The government, military, academia, smartly being care business, and private business not best gather, process, and store extraordinary amounts of data in our online global — as well as they rely on very important infrastructure systems in our online global to perform operations and send products and services and merchandise.
An attack on this infrastructure would possibly not best threaten purchaser data or a business’s bottom line — it’s going to moreover threaten a rustic’s protection, financial machine, and public coverage and smartly being.
Allowing for its importance, we’ve compiled this ultimate data on cybersecurity. Beneath, we’ll talk about what cybersecurity is precisely, how to protect your systems and information from attacks, and what resources to follow to stay up-to-date with emerging traits and technology related to cybersecurity.
Good cybersecurity involves a few layers of protection across the data, gadgets, methods, networks, and systems of an project. A mixture of technology and perfect imaginable practices can provide an effective coverage towards the frequently evolving and lengthening threats of our online global.
The ones threats include phishing, malware, ransomware, code injections, and additional. The have an effect on can vary depending on the scope of the attack. A cyber attack would perhaps end result inside the attacker making unauthorized purchases with an individual’s credit card data, or erasing a complete machine after injecting malware into an organization’s code base.
While even the most productive cybersecurity can’t give protection to towards every sort or instance of attack, it’s going to perhaps have the same opinion to minimize the hazards and have an effect on of such attacks.
Forms of Cybersecurity
Cybersecurity is a large period of time that can be broken down into further explicit subcategories. Beneath we will be able to walk through 5 number one types of cybersecurity.
Instrument Protection
Instrument protection, ceaselessly known as AppSec, is the follow of constructing, together with, and trying out security measures within information superhighway systems so that you can give protection to them towards attacks. Vulnerabilities, protection misconfigurations, and design flaws will also be exploited and result in malicious code injections, subtle data exposure, machine compromise, and other adversarial impacts.
AppSec is one of the most necessary types of cybersecurity because the application layer is basically essentially the most susceptible. In step with Imperva research, as regards to a part of data breaches over the past numerous years originated on the net application layer.
Cloud Protection
Cloud protection is a slightly contemporary type of cybersecurity. It’s the follow of shielding cloud computing environments along with systems operating in and information stored inside the cloud.
Since cloud providers host third-party systems, products and services and merchandise, and information on their servers, they’ve protection protocols and features in place — on the other hand consumers are also in part responsible and expected to configure their cloud provider appropriately and use it safely.
Essential Infrastructure Protection
Essential infrastructure protection is the follow of shielding the very important infrastructure of a space or nation. This infrastructure accommodates each and every physically and cyber networks, systems, and assets that provide physically and monetary protection or public smartly being and coverage. Call to mind a space’s electric power grid, hospitals, website guests lighting fixtures, and water systems as examples.
A large number of this infrastructure is digital or relies on the net somehow to function. It’s therefore vulnerable to cyber attacks and must be secured.
Internet of Problems (IoT) protection
Internet of Problems protection, or IoT protection, is the follow of shielding as regards to any instrument that connects to the tips superhighway and can keep up a correspondence with the group independently of human movement. This accommodates kid displays, printers, protection cameras, motion sensors, and a thousand million other gadgets along with the networks they’re associated with.
Since IoT gadgets gather and store personal knowledge, like a person’s determine, age, location, and smartly being data, they can have the same opinion malicious actors steal folks’s identities and must be secured towards unauthorized get right of entry to and other threats.
Group Protection
Group protection is the follow of shielding computer networks and information towards external and internal threats. Identification and get right of entry to controls like firewalls, virtual personal networks, and two-factor authentication can have the same opinion.
Group protection is most often broken down into 3 categories: physically, technical, and administrative. Each and every of these kind of group protection is about ensuring best the suitable folks have get right of entry to to group portions (like routers), data that is stored in or transferred by the use of the group, and the infrastructure of the group itself.
Cybersecurity Words to Know
Cybersecurity is a very intimidating subject, not no longer like cryptocurrency and artificial intelligence. It can be exhausting to snatch, and, frankly, it sounds kind of ominous and complicated.
On the other hand fear not. We’re proper right here to damage this subject down into digestible pieces that you just’ll rebuild into your own cybersecurity method. Bookmark this put as much as keep this handy word list at your fingertips.
Proper right here’s a whole file of overall cybersecurity words you should know.
Authentication
Authentication is the process of verifying who you could be. Your passwords authenticate that you just in reality are the one who should have the corresponding username. When you show your ID (e.g., motive force’s license, and so on), the fact that your symbol in most cases appears as should you is a way of authenticating that the determine, age, and care for on the ID belong to you. Many organizations use two-factor authentication, which we cover later.
Backup
A backup refers to the method of moving necessary data to a secure location like a cloud storage machine or an external exhausting drive. Backups will let you recuperate your systems to a healthy state in case of a cyber attack or machine crash.
Habits Monitoring
Habits monitoring is the process of staring on the movements of shoppers and gadgets in your group to recognize any possible protection events faster than they occur. Movements must not best be spotted however as well as measured towards baselines of usual behavior, traits, and organizational insurance coverage insurance policies and regulations.
As an example, you might follow and follow when shoppers log in and log out, within the match that they request get right of entry to to subtle assets, and what internet pages they seek advice from. Then say an individual tries to log in at an abnormal time, identical to the midnight. If that’s the case, you should identify that as abnormal behavior, read about it as a imaginable protection match, and finally block that log in try for those who suspect an attack.
Bot
A bot, temporary for robot, is an application or script designed to perform automated and repetitive tasks. Some bots have respected purposes, like chatbots that answer steadily asked questions on a internet web page. Others are used for malicious purposes, like sending direct mail emails or enticing in DDoS attacks. As bots grow to be further delicate, it’s going to get harder to tell the difference between superb bots and dangerous bots or even bots from human shoppers. That’s why bots pose an ever-growing risk to many of us and organizations.
CIA Triad
The CIA triad is a method that can be used to extend or assessment an organization’s cybersecurity systems and insurance coverage insurance policies.
The CIA triad refers to confidentiality, integrity, and availability. In follow, this taste promises data is disclosed best to authorized shoppers, remains right kind and trustworthy far and wide its lifecycle, and will also be accessed by the use of authorized shoppers when sought after without reference to instrument disasters, human error, and other threats.

Data Breach
A data breach refers again to the second one a hacker sure facets unauthorized get right of entry to or get right of entry to to a company’s or an individual’s data.
Digital Certificate
A digital certificate, ceaselessly known as an id certificate or public key certificate, is a kind of passcode used to safely change data over the tips superhighway. It’s essentially a digital file embedded in a device or piece of {{hardware}} that provides authentication when it sends and receives data to and from every other instrument or server.
Encryption
Encryption is the follow of using codes and ciphers to encrypt data. When data is encrypted, a computer uses a key to turn the tips into unintelligible gibberish. Only a recipient with the correct key is able to decrypt the tips. If an attacker gets get right of entry to to strongly encrypted data on the other hand doesn’t have the necessary factor, they aren’t in a position to see the unencrypted fashion.

HTTP and HTTPS
Hypertext Transfer Protocol (HTTP) is how web browsers communicate. You’ll in all probability see an http:// or https:// in front of the websites you seek advice from. HTTP and HTTPS are the identical, excluding HTTPS encrypts all data sent between you and the information superhighway server — subsequently the “S” for protection. In this day and age, as regards to all internet pages use HTTPS to strengthen the privacy of your data.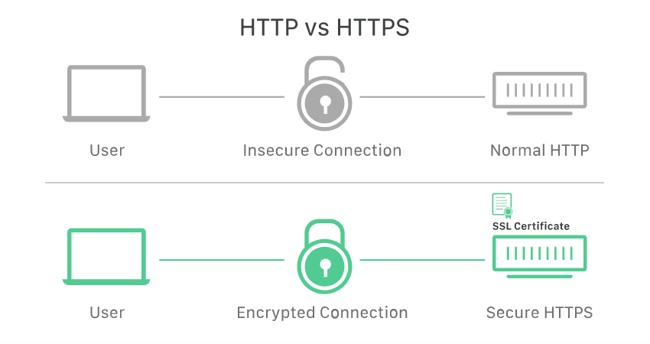
Vulnerability
A vulnerability is a place of vulnerable level {{that a}} hacker would perhaps exploit when launching a cyber attack. Vulnerabilities might be instrument bugs that want to be patched, or a password reset process that can be caused by the use of unauthorized folks. Defensive cybersecurity measures (like the ones we talk about later) have the same opinion be sure data is protected by the use of putting layers of protections between attackers and the problems they’re searching for to do or get right of entry to.
A cyber attack is a deliberate and most often malicious intent to snatch, regulate, or erase personal data. Cyber attacks are devoted by the use of external protection hackers and, on occasion, by chance by the use of compromised shoppers or staff. The ones cyber attacks are devoted for slightly a couple of reasons. Some are in search of ransom, while some are simply presented for fun.
Beneath we will be able to briefly move over the commonest cyber threats.
1. Password Guessing (Brute Power) Attack
A password guessing (or “credential stuffing”) attack is when an attacker frequently makes an try to wager usernames and passwords. This attack will steadily use recognized username and password combos from earlier data breaches.
An attacker is a good fortune when folks use inclined passwords or use the password between different systems (e.g., when your Facebook and Twitter password are the identical, and so on). Your perfect imaginable coverage towards this kind of attack is using tough passwords and heading off using the identical password in a few places along with using two component authentication, as we talk about later.)
2. Allocated Denial of Provider (DDoS) Attack
A distributed denial of service (DDoS) attack is when a hacker floods a group or machine with a ton of process (similar to messages, requests, or information superhighway website guests) so to paralyze it.
This is most often finished using botnets, which could be groups of internet-connected gadgets (e.g., laptops, delicate bulbs, game consoles, servers, and so on) infected by the use of viruses that allow a hacker to harness them into showing many types of attacks.
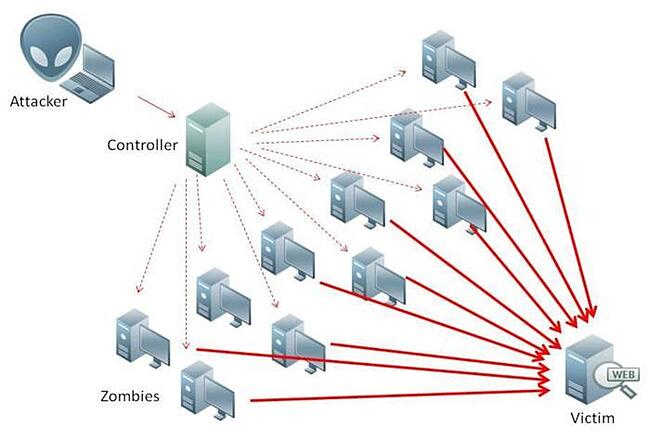
3. Malware Attack
Malware refers to all types of malicious instrument used by hackers to infiltrate laptop methods and networks and gather vulnerable personal data. Forms of malware include:
- Keyloggers, which follow the entire thing a person varieties on their keyboard. Keyloggers are in most cases used to snatch passwords and other personal knowledge, similar to social protection numbers.
- Ransomware, which encrypts data and holds it hostage, forcing shoppers to pay a ransom so to unlock and regain get right of entry to to their data.
- Spy ware, which displays and “spies” on individual process on behalf of a hacker.
Additionally, malware will also be delivered by way of:
- Trojan horses, which infect laptop methods through a apparently benign get right of entry to point, steadily disguised as a sound application or other piece of instrument.
- Viruses, which corrupt, erase, regulate, or snatch data and, now and again, physically hurt laptop methods. Viruses can spread from computer to computer, at the side of once they’re by chance installed by the use of compromised shoppers.
- Worms, which could be designed to self-replicate and autonomously spread through all similar laptop methods which will also be vulnerable to the identical vulnerabilities. .
4. Phishing Attack
A phishing attack is when hackers try to trick folks into doing something. Phishing scams will also be delivered through a apparently respected download, link, or message.
It’s a slightly commonplace type of cyber attack — 57% of respondents in a third-party survey said their organization experienced a successful phishing attack in 2020, up from 55% in 2019. And the have an effect on of a good fortune phishing attacks range from lack of expertise to financial loss.
Phishing is most often finished over piece of email or through a fake internet web page; it’s ceaselessly known as spoofing. Additionally, spear phishing refers to when a hacker makes a speciality of attacking a decided on person or company, as an alternative of making further general-purpose spams.
5. Man-in-the-Middle (MitM) Attack
A Man-in-the-Middle (MitM) attack is when an attacker intercepts communications or transactions between two occasions and inserts themselves inside the middle. The attacker can then intercept, manipulate, and steal data faster than it reaches its respected holiday spot. As an example, say a buyer is using a device on public WiFi that hasn’t been secured appropriately, or the least bit. An attacker would possibly exploit this vulnerability and insert themselves between the client’s instrument and the group to intercept login credentials, price card knowledge, and additional.
This sort of cyber attack is this type of good fortune because the victim has no concept that there’s a “man inside the middle.” It merely seems like they’re browsing the information superhighway, logging into their monetary establishment app, and so on.
%20Attack-p-500.jpeg?width=650&name=605cab5ff8f386ea033ae16c_Man-in-the-Middle)%20Attack-p-500.jpeg)
6. Cross Internet website Scripting Attack
A cross site scripting attack, or XSS attack, is when an attacker injects malicious code into an differently respected internet web page or application so to execute that malicious code in every other individual’s information superhighway browser.
Because of that browser thinks the code is coming from a depended on provide, it’s going to execute the code and forward knowledge to the attacker. This data is usually a session token or cookie, login credentials, or other personal data.
Here’s an illustrated example of an XSS attack:
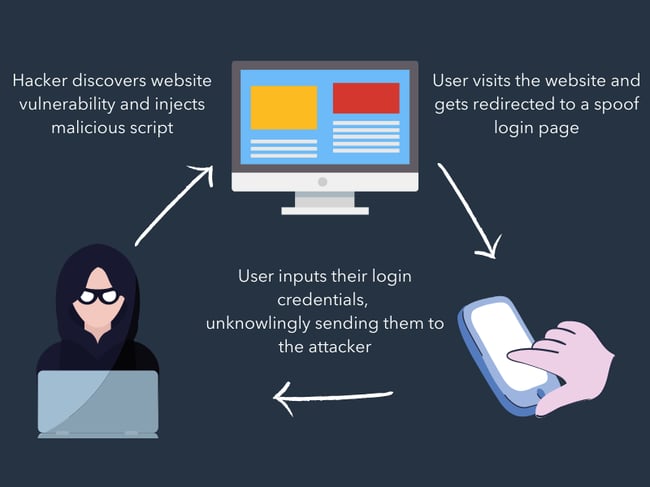
7. SQL Injection Attack
An SQL injection attack is when an attacker submits malicious code through an unprotected form or search box so to reach the ability to view and regulate the internet web page’s database. The attacker would perhaps use SQL, temporary for Structured Query Language, to make new accounts to your internet website, add unauthorized links and content material subject material, and edit or delete data.
This is a common WordPress security issue since SQL is the preferred language on WordPress for database regulate.
Cybersecurity Perfect Practices: Easy methods to Safe Your Data
Cybersecurity can’t be boiled down proper right into a 1-2-3-step process. Securing your data involves a mix of perfect imaginable practices and defensive cybersecurity tactics. Dedicating time and resources to each and every is among the perfect tactics to secure your — and your shoppers’ — data.
Defensive Cybersecurity Solutions
All firms should invest in preventative cybersecurity solutions. Enforcing the ones systems and adopting good cybersecurity habits (which we discuss next) will offer protection to your group and laptop methods from out of doors threats.
Proper right here’s a listing of five defensive cybersecurity systems and instrument alternatives that can prevent cyber attacks — and the inevitable headache that follows. Consider combining the ones solutions to cover your whole digital bases.
Antivirus Software
Antivirus instrument is the digital identical of taking that nutrition C boost all the way through flu season. It’s a preventative measure that displays for bugs. The method of antivirus instrument is to come back throughout viruses to your computer and remove them, very similar to nutrition C does when dangerous problems enter your immune machine. (Spoken like an actual scientific professional …) Antivirus instrument moreover indicators you to potentially unsafe information superhighway pages and instrument.
Be informed further: McAfee, Norton. or Panda (for free)
Firewall
A firewall is a digital wall that keeps malicious shoppers and instrument out of your computer. It uses a clear out that assesses the security and legitimacy of the entire thing that wants to enter your computer; it’s like an invisible judge that sits between you and the tips superhighway. Firewalls are each and every instrument and hardware-based.
Be informed further: McAfee LiveSafe or Kaspersky Internet Security
Single Sign-On (SSO)
Single sign-on (SSO) is a centralized authentication provider throughout which one login is used to get right of entry to a complete platform of accounts and instrument. Should you occur to’ve ever used your Google account to sign up or into an account, you’ve used SSO. Enterprises and corporations use SSO to allow staff get right of entry to to internal systems that contain proprietary data.
Be informed further: Okta or LastPass
Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a login process that requires a username or pin amount and get right of entry to to an external instrument or account, similar to an piece of email care for, phone amount, or protection instrument. 2FA calls for patrons to confirm their id through each and every and, on account of that, is far more secure than single component authentication.
Be informed further: Duo
Virtual Private Group (VPN)
A virtual personal group (VPN) creates a “tunnel” throughout which your data travels when entering and exiting a information superhighway server. That tunnel encrypts and protects your data so that it’s going to perhaps’t be be told (or spied on) by the use of hackers or malicious instrument. While a VPN protects towards spyware, it’s going to perhaps’t prevent viruses from entering your computer through apparently respected channels, like phishing or in all probability a fake VPN link. Because of this, VPNs should be blended with other defensive cybersecurity measures so that you can give protection to your data.
Be informed further: Cisco’s AnyConnect or Palo Alto Networks’ GlobalProtect
Cybersecurity Tips for Trade
Defensive cybersecurity solutions received’t art work excluding you do. To verify your corporation and purchaser data is protected, adopt the ones superb cybersecurity conduct all the way through your corporate.
Require tough credentials.
Require each and every your staff and shoppers (if appropriate) to create tough passwords. This will also be finished by the use of enforcing a character minimum along with requiring a mix of upper and lowercase letters, numbers, and symbols. Additional refined passwords are harder to wager by the use of each and every people and bots. Moreover, require that passwords be changed steadily.

Keep watch over and follow employee process.
Within your corporation, best give get right of entry to to necessary data to authorized staff who need it for their procedure. Prohibit data from sharing out of doors the crowd, require permission for external instrument downloads, and encourage staff to lock their laptop methods and accounts each and every time not in use.
Know your group.
With the rise of the Internet of Things, IoT gadgets are doping up on company networks like crazy. The ones gadgets, which aren’t underneath company regulate, can introduce chance as they’re steadily unsecured and run susceptible instrument that can be exploited by the use of hackers and provide a direct pathway into an internal group.
“Make sure you have visibility into all of the IoT gadgets to your group. The whole thing to your corporate group should be known, appropriately classified, and controlled. By way of understanding what gadgets are to your group, controlling how they connect to it, and monitoring them for suspicious movements, you’ll significantly reduce the landscape attackers are playing on.” — Nick Duda, Maximum necessary Protection Officer at HubSpot
Read about how HubSpot sure facets instrument visibility and automates protection regulate in this case study compiled by security software ForeScout.
Download patches and updates steadily.
Software vendors steadily unlock updates that care for and attach vulnerabilities. Keep your instrument secure by the use of updating it on a relentless basis. Consider configuring your instrument to exchange mechanically in order that you on no account forget.
Make it easy for group of workers to escalate issues.
If your employee comes all the way through a phishing piece of email or compromised information superhighway internet web page, you want to snatch instantly. Organize a machine for receiving the ones issues from staff by the use of dedicating an inbox to these notifications or rising a sort that individuals can fill out.
Cybersecurity Tips for Other folks
Cyber threats can have an effect on you as an individual consumer and knowledge superhighway individual, too. Adopt the ones superb conduct to protect your individual data and steer clear of cyber attacks.
Mix up your passwords.
The use of the identical password for your whole necessary accounts is the digital identical of leaving a spare key underneath your front doormat. A recent study came upon that over 80% of data breaches have been a result of inclined or stolen passwords. Even if a business or instrument account doesn’t require a formidable password, always make a selection person who has a mix of letters, numbers, and symbols and change it steadily.
Observe your monetary establishment accounts and credit score rating frequently.
Assessment your statements, credit score rating studies, and other very important data steadily and report any suspicious process. Additionally, best unlock your social protection amount when utterly necessary.
Be intentional online.
Keep an eye fixed fastened out for phishing emails or illegitimate downloads. If a link or internet web page turns out fishy (ha — get it?), it in all probability is. Seek for dangerous spelling and grammar, suspicious URLs, and mismatched piece of email addresses. In spite of everything, download antivirus and protection instrument to come up with a caution of possible and recognized malware assets.
Once more up your data steadily.
This habit is very good for corporations and people to snatch — data will also be compromised for each and every occasions. Consider backups on each and every cloud and physically puts, similar to a troublesome drive or thumb drive.
Why You Must Care About Cybersecurity
In step with a report by RiskBased Security, there were 3,932 data breaches reported in 2020, which exposed over 37 billion data. Moreover, a modern know about came upon that the global average worth of a data breach amounted to 3.86 million U.S. dollars in 2020. That suggests the cost of data breaches amounted to kind of 15.2 billion dollars final 12 months.
Small to medium-sized firms (SMBs) are in particular at risk. Likelihood is that you’ll see corporations like Function and Sears topping the headlines as perfect data breach victims, on the other hand it’s in reality SMBs that hackers need to focal point on.
Why? They’ve further — and additional precious — digital assets than your average consumer on the other hand a lot much less protection than a larger enterprise-level company … putting them right kind in a “hackers’ cybersecurity sweet spot.”
Protection breaches are frustrating and horrifying for each and every firms and consumers. In a survey by Measure Protocol, kind of 86% of respondents mentioned that contemporary privacy breaches inside the data had impacted their willingness to share personal knowledge to some extent.
On the other hand cybersecurity is about further than just heading off a PR nightmare. Investing in cybersecurity builds believe in conjunction with your shoppers. It encourages transparency and reduces friction as shoppers grow to be advocates to your logo.
“Everyone has a task in helping to protect shoppers’ data. Proper right here at HubSpot, every employee is empowered to unravel for purchaser needs in a secure and secure way. We want to harness everyone’s energy to offer a platform that consumers believe to accurately and safely store their data.” — Chris McLellan, HubSpot Chief Protection Officer
Cybersecurity Belongings
The resources underneath will will can help you be told further about cybersecurity and learn how to upper equip your corporation and group of workers. We moreover recommend checking out necessarily essentially the most popular cybersecurity podcasts and cybersecurity blogs, too.
National Institute of Necessities and Era (NIST)
NIST is a government corporate that promotes excellence in science and business. It moreover comprises a Cybersecurity department and routinely publishes guides that necessities.
Bookmark: The Computer Protection Helpful useful resource Center (CSRC) for protection perfect imaginable practices, referred to as NIST Special Publications (SPs).
The Center for Internet Protection (CIS)
CIS is a world, non-profit protection helpful useful resource and IT group used and depended on by the use of professionals inside the field.
Bookmark: The CIS Top 20 Critical Security Controls, which is a prioritized set of perfect imaginable practices created to stop necessarily essentially the most pervasive and dangerous threats of these days. It was developed by the use of major protection professionals from all over the world and is delicate and validated every year.
Cybrary
Cybrary is a web based cybersecurity education helpful useful resource. It supplies maximum recurrently unfastened, full-length instructional films, certifications, and additional for all kinds of cybersecurity topics and specializations.
Bookmark: The Certified Information Systems Security Professional (CISSP) 2021, which is the latest trail for information protection professionals. Earning this “gold usual” of protection certifications will set you excluding other knowledge protection professionals.
The Cyber Readiness Institute
The Cyber Readiness Institute is an initiative that convenes business leaders from different sectors and spaces to share resources and information to finally advance the cyber readiness of small and medium-sized firms.
Bookmark: The Cyber Readiness Program, which is a unfastened, online program designed to have the same opinion small and medium-sized enterprises secure their data, staff, vendors, and shoppers towards these days’s most not unusual cyber vulnerabilities.
Signing Off … Securely
Cyber attacks could also be intimidating, on the other hand cybersecurity as an issue doesn’t want to be. It’s an important to be in a position and armed, in particular for those who’re coping with others’ data. Firms should commit time and resources to protecting their laptop methods, servers, networks, and instrument and should stay up-to-date with emerging tech.
Coping with data with care best makes your corporation further trustworthy and transparent — and your shoppers further loyal.
Remember: Any legal knowledge in this content material subject material isn’t the identical as legal advice, where an attorney applies the law to your explicit circumstances, so we insist that you just search the recommendation of an attorney for those who’d like advice to your interpretation of this data or its accuracy. In a nutshell, you received’t rely on this as legal advice or as a recommendation of any specific legal understanding.
Editor’s understand: This publish was firstly published in February 2019 and has been up-to-the-minute for comprehensiveness.
![]()
Contents
- 1 Forms of Cybersecurity
- 2 Cybersecurity Words to Know
- 2.1 Authentication
- 2.2 Backup
- 2.3 Habits Monitoring
- 2.4 Bot
- 2.5 CIA Triad
- 2.6 Data Breach
- 2.7 Digital Certificate
- 2.8 Encryption
- 2.9 HTTP and HTTPS
- 2.10 Vulnerability
- 2.11 1. Password Guessing (Brute Power) Attack
- 2.12 2. Allocated Denial of Provider (DDoS) Attack
- 2.13 3. Malware Attack
- 2.14 4. Phishing Attack
- 2.15 5. Man-in-the-Middle (MitM) Attack
- 2.16 6. Cross Internet website Scripting Attack
- 2.17 7. SQL Injection Attack
- 3 Cybersecurity Perfect Practices: Easy methods to Safe Your Data
- 4 Cybersecurity Tips for Trade
- 5 Cybersecurity Tips for Other folks
- 6 Why You Must Care About Cybersecurity
- 7 Cybersecurity Belongings
- 8 Signing Off … Securely
- 9 Learn how to construct a Gutenberg plugin so as to add capability to the block editor
- 10 5 Best WordPress Podcast Plugins in 2023
- 11 Be told Excel On-line: 21 Loose and Paid Assets for Excel Coaching





0 Comments