Organizations rely on a lot of online apps and products and services and merchandise daily, each and every of which requires different logins, making password keep an eye on a emerging downside.
Your crew can profit from a CRM, an intranet, a work chat, and other third-party products and services and merchandise, corresponding on your web website hosting provider’s dashboard, on a daily basis. If this sounds familiar, you more than likely want a centralized authentication mechanical device that allows your crew contributors to use the equivalent login credentials all over a lot of internet pages and platforms.
That’s the position Single Sign-On (SSO) is to be had in, as a solution designed to streamline authentication, make stronger protection, and support the efficiency of your crew’s workflows. For online corporations, SSO is bigger than just a nice-to-have serve as. It is a tricky instrument that imply you’ll strengthen your corporate’s protection and support business processes.
SSO integration with the MyKinsta dashboard using Protection Observation Markup Language (SAML) is designed in particular for this purpose: it centralizes get entry to keep watch over with major Identity Providers, automates the onboarding process by way of JIT provisioning, and strengthens the safety of your web website hosting account and your customers’ data.
This article explores SAML SSO in its key sides. You’re going to be told what it’s and why it’s non-negotiable for adopting a zero-trust coverage in your enterprise.
There’s so much to cover, so let’s get started!
What SAML SSO is and how it works
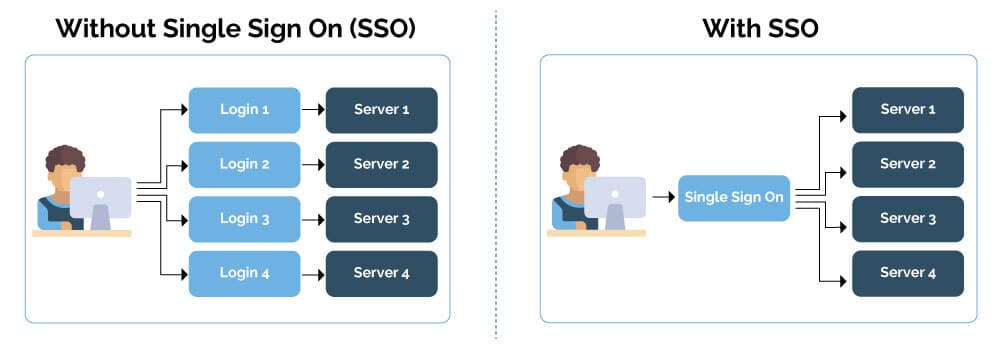
SAML SSO is an authentication scheme that permits a client to soundly log in to a few independent programs or instrument products and services and merchandise using a single set of credentials. Consumers don’t need to store or organize a few passwords for more than a few products and services and merchandise; they just need to log in to unquestionably certainly one of them to get entry to the others securely.
An SSO mechanical device has two key actors: the supplier provider and the identity provider.
- The supplier provider (SP) is the applying, web supplier, or helpful useful resource an end-user needs to get entry to. It may be an intranet, a CRM, or a third-party supplier.
- The identity provider (IdP) is a supplier or mechanical device that creates, maintains, and manages identity knowledge and gives authentication products and services and merchandise to third-party products and services and merchandise.
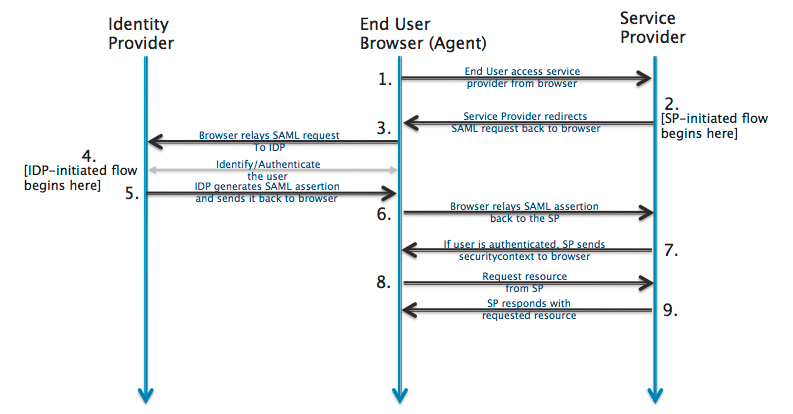
Proper right here’s how it works:
- A client makes an try to log in to an software, comparable to a WordPress web site or your web website hosting provider’s dashboard.
- If the applying (the SP) detects that the patron isn’t authenticated, it redirects the patron to the Identity Provider.
- The IdP then turns on the patron to log in with their credentials.
- The IdP verifies the patron credentials. In the event that they’re right kind, the IdP authenticates the patron and generates a security token.
- The IdP sends the safety token to the SP.
- The SP receives the token, validates it, and grants the patron get entry to.
Listed here are some common IdPs:
- Microsoft Entra ID: Microsoft’s cloud-based identity and get entry to keep an eye on supplier. Designed for seamless integration with Microsoft 365 and Azure products and services and merchandise, it can be integrated with masses of SaaS programs. It is helping SAML, OAuth 2.0, and OpenID Connect protocols, along with various authentication methods.
- Google Id Platform: A scalable and secure identity and get entry to keep an eye on resolution according to Google’s international infrastructure. It is helping industry-standard authentication protocols, comparable to SAML, OAuth 2.0, and OpenID Connect.
- Okta: An enterprise-grade identity keep an eye on supplier. Okta is helping the most typical authentication protocols, comparable to Kerberos, LDAP, OAuth 2.0, RADIUS, and SAML.
- Auth0: Now a part of Okta, Auth0 is an identity and get entry to keep an eye on platform with pleasant flexibility and customization alternatives for developers to build custom designed programs. It is helping industry-standard protocols, in conjunction with OpenID Connect, SAML, OAuth 2.0, WS-Federation, LDAP, and extra.
- Keycloak: An open-source Identity and Get right to use Regulate (IAM) resolution complicated by means of Red Hat and introduced beneath Apache License 2.0. It’s according to conventional protocols and is helping OpenID Connect, OAuth 2.0, and SAML.
SAML SSO is ceaselessly confused with social login, alternatively there are key diversifications between the two. Social login is a selected implementation of single sign-on, however it has important diversifications and explicit use circumstances.
Similar to Kinsta SAML SSO, social login lets in shoppers to get entry to a few products and services and merchandise with a single identity managed by means of an identity provider. With social login, the identity provider (IdP) is a social group, comparable to Facebook, Google, or GitHub.
The two authentication tactics are an identical in that they every use now not abnormal protocols, comparable to OAuth 2.0 and OpenID Connect, to permit authentication through a single supplier provider. In every scenarios, the authentication experience and the control of get entry to credentials are considerably enhanced, as are mechanical device protection and the productivity of the IT crew.
On the other hand, there are important diversifications between the two tactics.
B2B vs B2C: SSO is an authentication and identity keep an eye on mechanical device designed necessarily for firms. Social login is a type of SSO geared toward shoppers and used in third-party programs or internet pages.
Public platforms vs within or faithful IdPs: The type of IdP may be different. For social login, the IdP is a social group or public platform. For project SSO, the identity provider can be an within mechanical device or a loyal IdP, comparable to Okta, Auth0, or Microsoft Entra ID.
Accessibility and keep watch over: Social login IdPs are shopper platforms accessible to someone with an account and don’t require complicated configuration by means of a skilled IT crew.
Conversely, SSO involves mechanical device configuration and identity keep an eye on, which fall inside an organization’s responsibility. The gang determines what data to share, which protocols to use, and which protection insurance coverage insurance policies to adopt (like two-factor authentication).
Data sharing: With social login, supplier providers can share shopper data according to the permissions granted.
On the other hand, typical SSO best possible shares the ideas necessary for authentication and authorization without exposing non-public knowledge.
Why SSO is essential for modern organizations
SSO is a key part in in recent times’s digital ecosystem. It enhances protection, improves the patron experience, and streamlines shopper keep an eye on.
Solid protection
SSO centralizes identity keep an eye on in a secure and specialized mechanical device: the IdP. To put it simply, on account of SSO, your internet web page not needs to keep an eye on the authentication process without delay on account of this responsibility is delegated to the IdP. This reduces the hazards associated with the improper keep an eye on of login knowledge and accounts. Let’s take a greater look.
Prone passwords: With SSO, you not need to create and store plenty of secure passwords. The only set of credentials you wish to have is from the IdP, which most often has clear and strict password insurance coverage insurance policies, which makes problems much more secure.
Credential stuffing: One of the vital now not abnormal password keep an eye on mistakes is using the equivalent password all over different online products and services and merchandise. This may build up a mechanical device’s basic vulnerability on account of, if one internet web page is hacked, the equivalent combination of credentials can be used to get entry to other web sites. These kind of attacks are known as credential stuffing.
Because of SSO, shoppers don’t need to reuse the equivalent credentials to get entry to a few web products and services and merchandise. When a client logs in to a web supplier by way of SSO, that supplier does now not download or store the patron’s password. Because of this truth, a possible attack would now not expose your shoppers’ login credentials. This reduces the attack ground dramatically, eliminating the chance of password theft.
What happens if the IdP is compromised? Since the IdP is the only de-provisioning stage, it’s typically the only keep watch over stage for disabling hacked accounts. As soon as a breach is detected, the administrator can disable the account, fighting all attached programs (SPs) from being breached.
Theft of credentials from insecure tactics: Internet websites with susceptible safety features can store passwords in an unencrypted or just reversible construction.
With SSO, you could be delegating the responsibility of managing and storing your credentials to the IdP, which specializes in secure storage and employs {{industry}} best practices for credential protection.
Phishing and machine-in-the-middle attacks: A phishing attack is an attempt to scouse borrow refined knowledge, comparable to usernames, passwords, credit card numbers, or monetary establishment details, for use or sale with malicious intent. A an identical state of affairs occurs with a machine-in-the-middle attack, where an attacker inserts themselves into the dialog channel between two devices.
Most often, IdPs offer sophisticated security features, comparable to multi-factor authentication (MFA) and fraud detection. As a result of this even though a client provides their credentials to a malicious actor, a second authentication part blocks get entry to. Additionally, secure protocols like SAML and OIDC offer protection to communications between shoppers, supplier providers, and identity providers.
Inefficient onboarding and de-provisioning: When a client leaves the gang, some accounts would most likely keep unnecessarily vigorous. This may create susceptible spots throughout the mechanical device’s protection.
With SSO, the de-provisioning process is centralized. Disabling the patron throughout the IdP blocks their get entry to to all attached products and services and merchandise.
Complicated shopper experience
With SAML SSO, a single login routinely authenticates shoppers all over all products and services and merchandise, granting them get entry to to all the property throughout the ecosystem.
This moreover boosts crew member productivity. Consumers can in brief switch between programs without interruption, eliminating the time it takes to enter or retrieve passwords. Fewer logins moreover indicate fewer authentication errors, fewer password resets, and less artwork for IT departments.
For online business householders, SSO isn’t only a delightful serve as to have; it’s a strategic instrument that without delay impacts business protection and shopper experience.
Upper productivity and diminished working costs
SAML SSO provides considerable benefits in terms of operational efficiency and long-term business sustainability:
Reduced load on IT departments: One of the vital now not abnormal pitfalls of credential keep an eye on is shoppers forgetting their passwords or making a few login makes an strive with improper credentials. This ceaselessly leads to toughen requests to IT puts of labor for password resets. The ones requests represent a worth in terms of time and property.
By means of enforcing SSO, shoppers best possible need to organize one password. Because of this, there are fewer toughen requests, and the IT crew can focal point on strategic movements, comparable to technological innovation and infrastructure protection.
Simplified shopper keep an eye on: In massive, complicated organizations, shopper keep an eye on is a specifically burdensome procedure. Consider a company that uses dozens of more than a few programs. Without SSO, every time a brand spanking new crew member joins the gang, they are going to need to create a brand spanking new account for each and every software in use.
When an employee leaves, you’ll have to delete their account from all of the ones products and services and merchandise. This process is cumbersome, and inadvertently leaving an vigorous shopper account on a supplier can create protection gaps. With SSO, there is no need to concern about this. Merely create one account, and the patron can instantly get entry to all products and services and merchandise.
De-provisioning may be fast and secure because you best possible need to delete one account to disconnect the patron from all products and services and merchandise throughout the crew.
Streamlined supplier integration: Individual keep an eye on is the most important and complicated side of software development. On each and every instance you introduce a brand spanking new supplier into your corporate, you’ll have to develop a brand spanking new mechanical device for authenticating and managing shopper accounts.
With identity keep an eye on protocols comparable to SAML and OpenID Connect, integrating SSO into your mechanical device is relatively easy on account of your software does now not want to take care of identity keep an eye on, allowing your IT department to pay attention to the strategic choices of your core business.
Centralized get entry to keep watch over: With many products and services and merchandise in use, controlling who has get entry to to each and every of the ones products and services and merchandise is a troublesome procedure for IT administrators.
SAML SSO solves this downside by means of providing a single stage of get entry to to all products and services and merchandise. From a single central stage, admins can observe shopper get entry to and task, along with find protection holes, all from a single dashboard. The end result’s an higher capacity to keep watch over get entry to and a sooner response time in case of incidents.
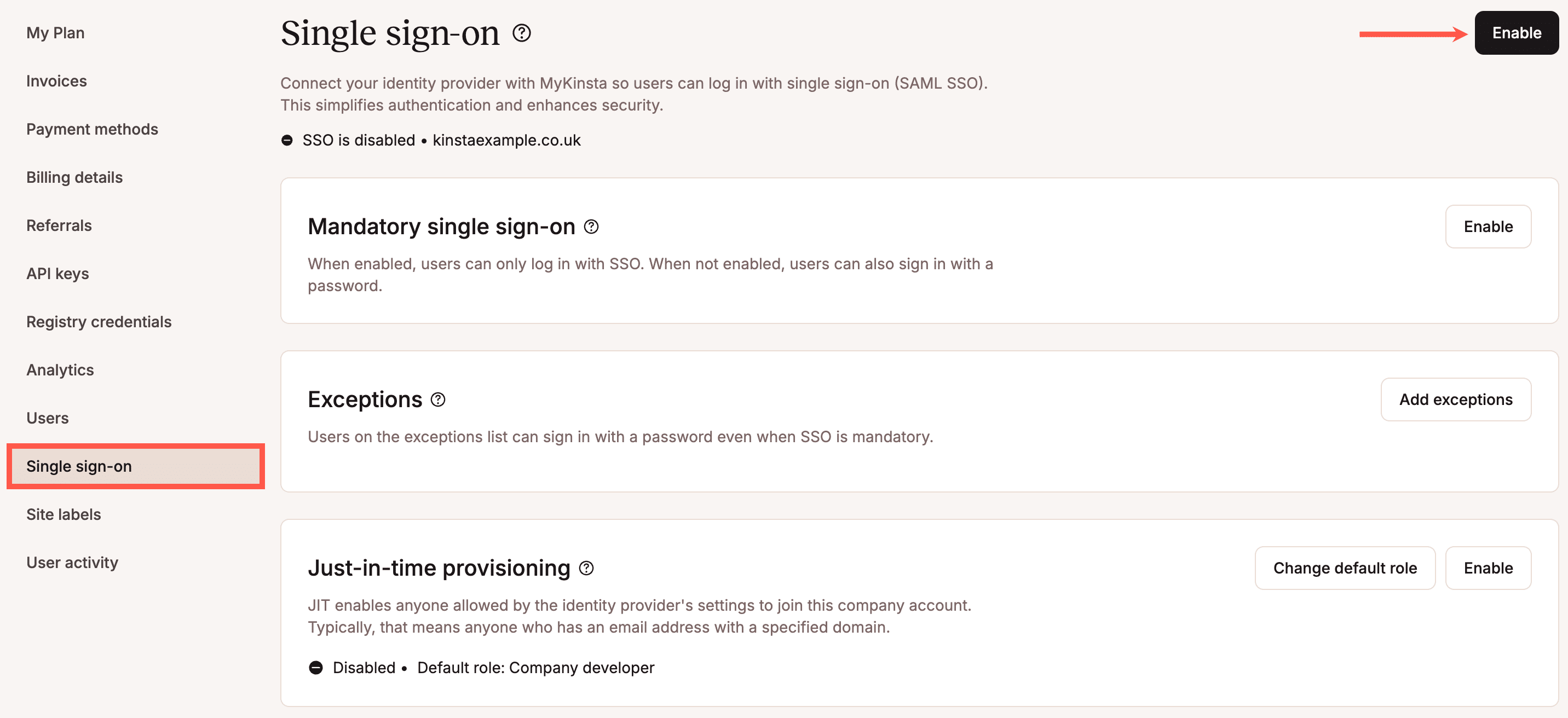
Kinsta SAML SSO authentication
MyKinsta is helping the XML-based SAML protocol to permit the secure business of authentication and authorization data between an IdP and an SP.
As a result of this Kinsta’s consumer corporations can add single sign-on capacity and protection to their web website hosting dashboard.
Using SSO with MyKinsta is best for firms with emerging teams, as it removes the trouble of guide get entry to keep an eye on and streamlines all the onboarding, shopper keep an eye on, and offboarding process.
Centralized identity keep an eye on and granular get entry to keep watch over
By means of enabling Kinsta SAML SSO, corporations can combine centralized identity keep an eye on with the MyKinsta multi-user dashboard.
The IdP acts as single provide of truth. Proper right here, corporations decide which crew contributors can get entry to their Company account in MyKinsta.
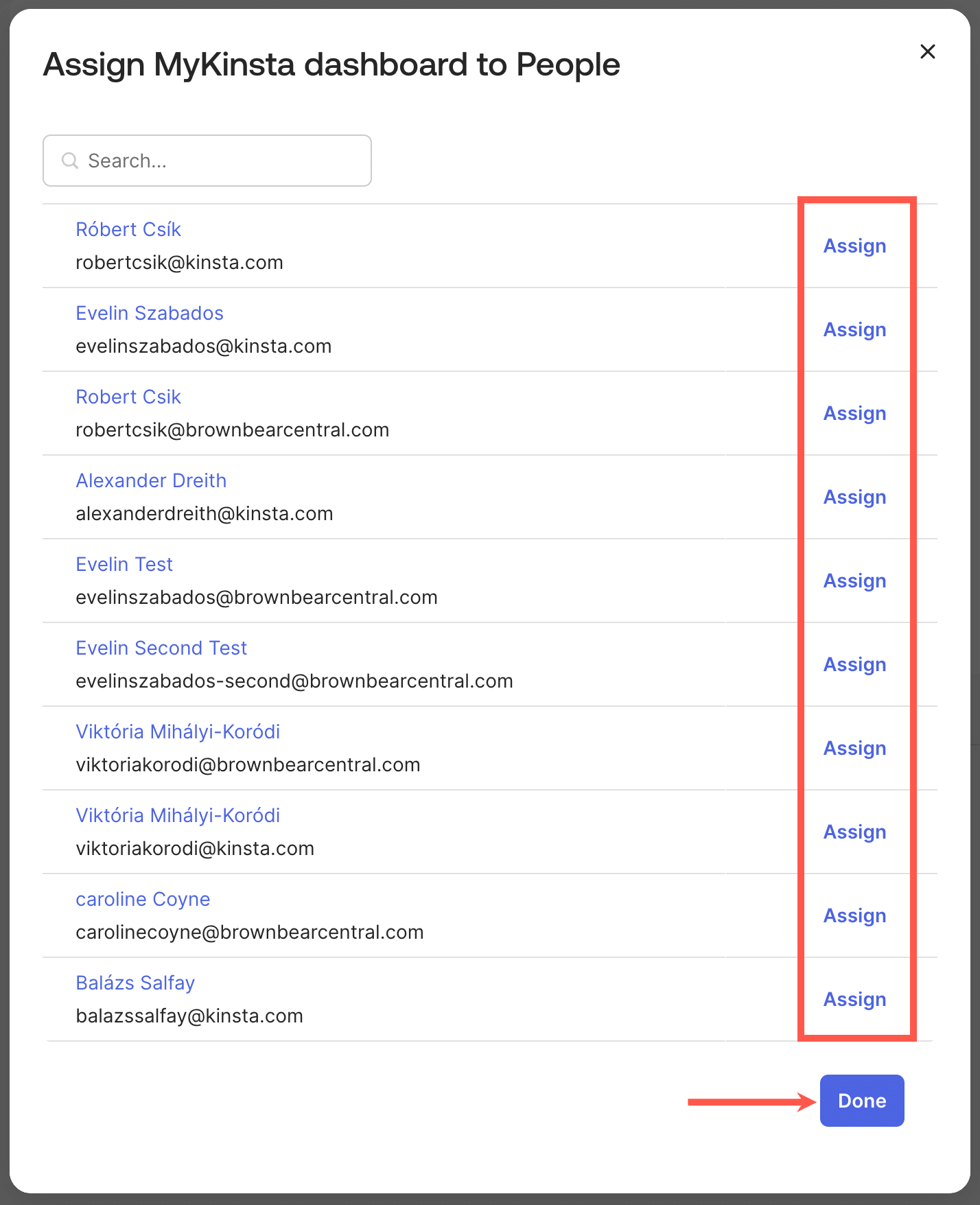
MyKinsta is your middle for granular shopper keep watch over. When shoppers log in to MyKinsta, they’re assigned a default place. This can be modified later by means of the Company owner or administrators.
Enabling Kinsta SAML SSO enhances protection by means of protecting your corporate account with the IdP’s protection insurance coverage insurance policies, in conjunction with multi-factor authentication and stringent password prerequisites. Additionally, Company account shoppers not need to use their login credentials, which minimizes the chance of credential theft.
Merely-in-time provisioning with Kinsta SAML SSO
MyKinsta is helping just-in-time (JIT) provisioning, which helps you to routinely create a brand spanking new MyKinsta shopper account when a client logs in for the main time by way of SAML SSO.
When JIT provisioning is enabled, approved shoppers at the IdP can without delay get entry to MyKinsta without having a guide invitation or a separate shopper account. This means approved shoppers best possible need an electronic mail take care of in conjunction with your company’s house to get entry to your MyKinsta account.
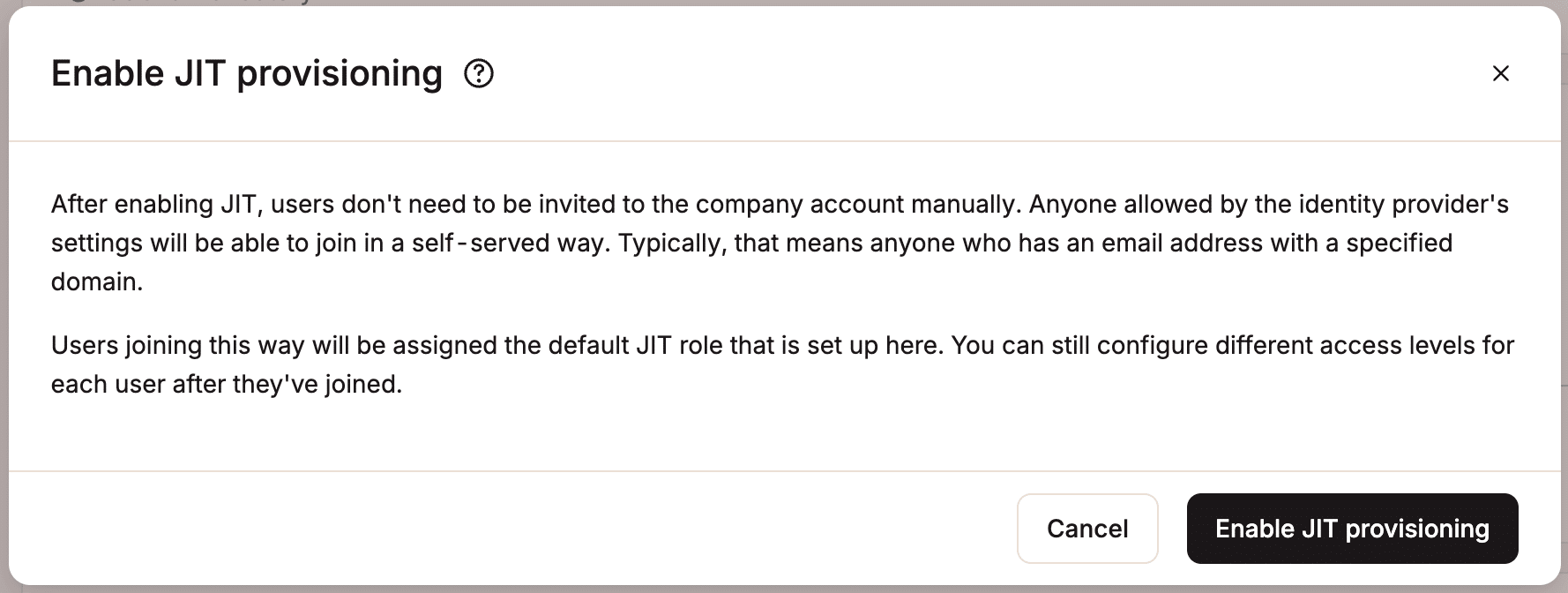
By means of default, crew contributors who get entry to MyKinsta by way of JIT provisioning are assigned the Company Developer place. Company householders and administrators can trade a client’s place once they join or alter the default place for new JIT-provisioned shoppers previous than the patron joins.
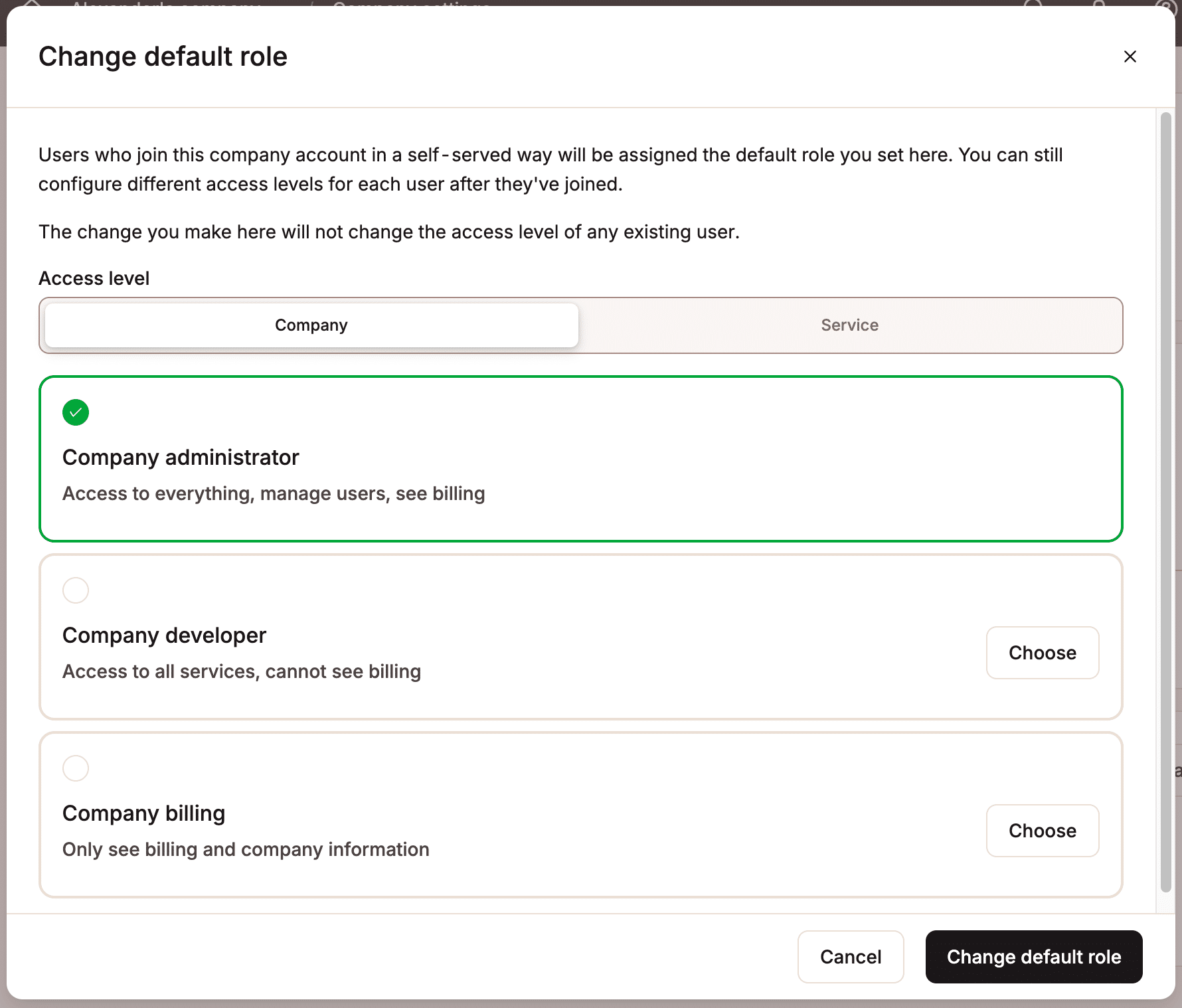
By means of automating the onboarding process, corporations and other organizations can significantly reduce the time and effort hooked in to onboarding and shopper keep an eye on processes. This permits them to in brief respond to purchaser requests by means of scaling their crew with minimal effort.
Environment friendly deprovisioning
For an organization that adopts a zero-trust philosophy, you will need to to in brief and securely revoke get entry to for purchasers who leave the gang. Environment friendly deprovisioning may be the most important to verify compliance with data protection and privacy regulations.
When a client leaves the gang, the gang administrator should delete the patron’s account from the identity provider. On the other hand, when JIT provisioning is enabled, revoking a client’s get entry to at the IdP isn’t enough, and likewise you’ll have to remove them from every the IdP and MyKinsta. Simply eliminating them from the IdP received’t artwork, as they’re going to nevertheless be capable to get entry to your company account with their MyKinsta credentials.
Regulatory compliance
So to agree to protection regulations and acquire certifications comparable to SOC2 and ISO 27001, organizations should expose that they’ve strict get entry to keep watch over measures in place. Adopting Kinsta SAML SSO promises compliance with the ones prerequisites because it guarantees that protection insurance coverage insurance policies are carried out consistently all over all attached products and services and merchandise.
Kinsta SAML SSO may be appropriate with regulations such for the reason that GDPR, as it tracks get entry to to personal data and promises the respect of the principles of information minimization and well timed revocation of get right of entry to through fast deprovisioning.
Summary
Kinsta’s SAML SSO authentication serve as complements the multi-user purposes of the MyKinsta dashboard. Companies can streamline their workflows by means of combining granular shopper keep an eye on for the company account with SSO identity and get entry to keep an eye on, automating a large number of the onboarding process and enhancing account protection.
Account administrators can assign predefined roles to provisioned shoppers, make exceptions to the IdP provisioning process, and block get entry to to precise shoppers. For corporations with dozens of developers and crew contributors in a lot of roles, Kinsta SAML SSO is essential for enhancing protection, flexibility, and operational efficiency.
Curious to try our best price managed WordPress web website hosting? Check out Kinsta at no cost lately!
The post Kinsta SAML SSO is right here: Scale your company quicker and extra securely appeared first on Kinsta®.
Contents




0 Comments